TSCM - "Dusting", microphone and spy camera detection
Technical Surveillance Counter Mesures
Context and Security Challenges
The current environment is characterized by a significant increase, indeed an intensification, of offensive techniques related to industrial espionage, economic interference, and the illicit collection of information. Furthermore, the private and professional spheres are increasingly targeted by individuals or organizations seeking to gather data for the purpose of blackmail or manipulation.
In the face of these critical economic and strategic challenges, it is imperative to address the question of effective security across all levels of your organization against malicious recording and eavesdropping.
Intervention
The necessity of professional TSCM expertise is driven by essential strategic and legal imperatives. The primary objectives include:
I. Protection of Assets and Strategic Information
* Detection and Neutralization of clandestine listening and recording devices.
* Protection of trade secrets and prevention of infringements on intellectual property.
* Preservation of the entity’s reputation and limitation of potential financial damages.
* Maintenance of absolute confidentiality for all commercial and strategic negotiations.
* Safeguarding of patents, internal processes, and data that constitute the competitive advantage.
* Protection of emerging and innovative technologies.
II. Regulatory Compliance and Operational Security
* Guarantee of GDPR compliance and adherence to personal data protection protocols.
* Reduction of litigation risk associated with the leakage or theft of confidential information.
* Prevention of sabotage attempts and operational disruptions.
* Strengthening the trust and credibility with clients and partners.
* Protection of employee privacy (Legal compliance and employer obligation).
* Blocking of electronic attack vectors susceptible to exploiting physical vulnerabilities.
Operational Deployment of Electronic Countermeasures (ECM / TSCM)
Principles of Intervention
In strict adherence to an exhaustive and rigorous procedure, and utilizing solely high-technology investigation equipment, CAPHEX conducts Electronic Countermeasures (ECM) operations, also known by the term Technical Surveillance Counter-Measures (TSCM).
These interventions aim to detect, locate, and neutralize any system for clandestine listening, transmission, or recording (commonly referred to as « bugs » or « micro-spies ») within your sensitive environments: professional premises (offices, meeting rooms), private residences, and all modes of transport (vehicles, private jets, and yachts).
Comprehensive Inspection and Audit Procedure (The « Sweeping »)
We are equipped to provide a complete TSCM/ECM inspection, often designated as a « sweeping » audit, which is meticulously adapted to your operational imperatives, expectations, and constraints.
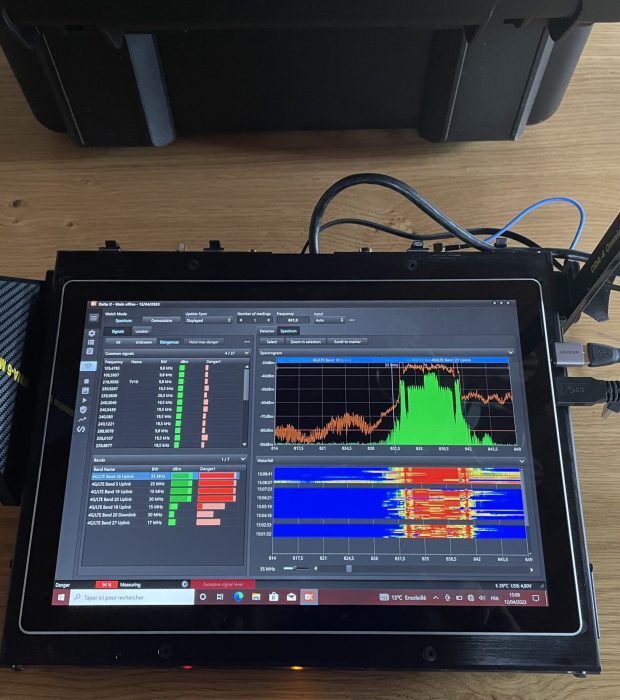






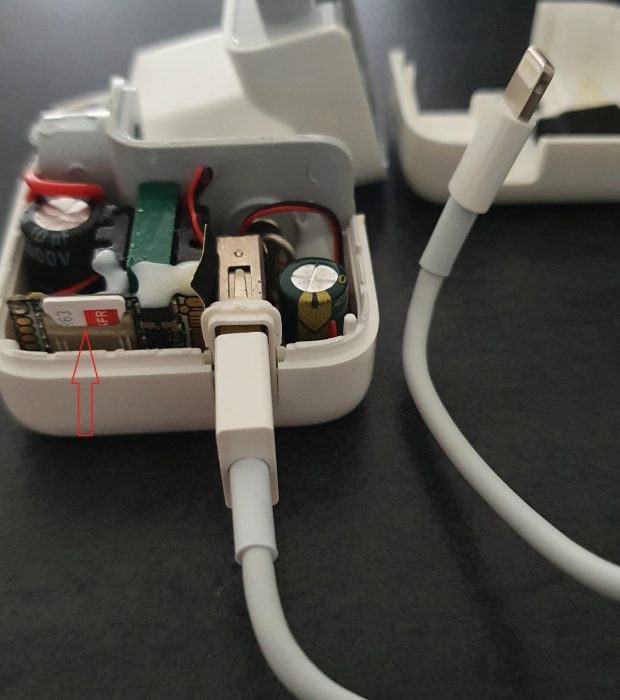











List of checks
Detailed TSCM Audit Procedures
From 0 to 24 GHz (voice, data and géolocalisation)
I. Audit of Telephone Lines and Communication Channels
The inspection of communication infrastructures is conducted across an extended frequency spectrum from 0 to 24 GHz and covers all transmission vectors (voice, data, and trackers).
Essential verifications include:
* Integrity Control of Stations and Network: Verification and analysis of each telephone station (landlines, VoIP) and its network connections, including the control of associated telephone and power cables.
* Interface Inspection: In-depth examination of each analog and digital telephone jack to detect any physical alteration or modification.
* Detection of Line Interception Devices: Search for all types of integrated analog or digital bugs, serial or parallel configurations (specifically devices known as « bridging » or tap devices).
* Search for Inductive and Passive Eavesdropping: Identification of line taps and passive eavesdropping via induction.
* Analysis of Concealed Channels: Search for systems utilizing Power Line Communication (PLC), autonomous recorders, or any other material enabling remote ambient listening or encrypted transmission.
* Analysis of Media Confidentiality: Examination of the isolation and integrity of telecommunication cabling (insulation study) to identify signal leakage.
II. Audit of Physical
Environments (Offices and Meeting Rooms)
The audit of sensitive spaces is a multi-spectral inspection aimed at detecting all concealed devices:
* Search for Emitting Devices: Detection of analog and digital microphones, infrared devices, laser transmitters, and wired listening systems (stethoscopes).
* Verification of Video Systems: Search for wired and wireless video surveillance systems (mini-cameras), accompanied by an analysis of vulnerable entry points (windows, bays, false ceilings, electrical installations, heating, ventilation, and air conditioning ducts, etc.).
* Inspection of Recording Systems: Search for autonomous and clandestine recording systems (MP3, digital recorders, etc.).
* Detection of Clandestine Power Sources: Search for self-powered microphones utilizing Power Line Communication (PLC) or other concealed energy sources.
* Audit of Building Infrastructure: In-depth verifications of power cables, electrical and telephone outlets, video surveillance equipment, and videoconferencing systems (potential vectors for implantation).
* Control of Furniture and Environment: Inspection of furniture, decorative accessories, and household appliances (frequent vectors for concealment).
* Cyber-Physical Terminal Audit: Verification of the integrity of mobile phones and computers (search for sophisticated spyware such as advanced monitoring software).
« Absolute trust. Secure environment« , so do not hesitate to consult us for more information.
A TSCM operation is also possible on your motor vehicle, yacht, aircraft or any other motor vehicle. Similarly, CAPHEX is able to perform Forensic analysis on your phones and laptops, as well as detect the installation of malware and spyware (PEGASUS). Do you have a pressing need to secure a room for an important meeting? CAPHEX can also protect your place of exchange by implementing effective means of interception.
Follow us on LinkedIn

Integrated safety solutions & TSCM expertise
40 rue Laure Diébold – 69009 Lyon FRANCE
SIREN : 852 508 985
Version EN1
2019 – 2023 © CAPHEX
40 rue Laure Diébold – 69009 Lyon FRANCE


